Networks
Networks have become a fundamental part of today's information systems. They form the pillar in the sharing of information in companies as well as in government and scientific groups
This information can take different forms, be it as documents, data to be processed by another computer, files sent to colleagues, and even more exotic forms of data
History
Most of these networks were installed in the late 1960s and 1970s, when network design was regarded as the philosopher's stone of computer research and cutting-edge technology. It resulted in numerous network models such as packet switching technology, collision-sensing local area networks (LANs), hierarchical enterprise networks, and many other high-quality networks
Since the early 1970s, another aspect of networking technology has gained importance: the protocol stack model, which enables interoperability between applications. A whole range of architectures was proposed and implemented by various research teams and computer manufacturers
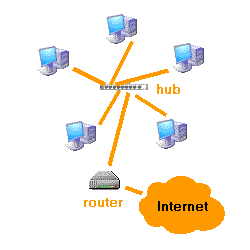
The result of all this practical knowledge is that today any group of users can find a physical network and architecture appropriate to their specific needs, from low-cost asynchronous lines, without any other error recovery method than a bitwise parity function, to full functions of wide area networks (WAN , public or private) with reliable protocols such as public packet switching networks or SNA private networks, up to local area networks, high speed but limited distance
The downside of this information explosion is the distressing situation that occurs when a group of users wants to extend their computer system to another group of users, which turns out to have different technology and network protocols. Consequently, even if they could agree on the type of network technology to physically connect their facilities, applications (such as mail systems) would still be unable to communicate with each other due to different protocols
He became aware of this situation quite early (in the early 1970s), thanks to a group of researchers in the United States, who were the architects of a new paradigm: networking. Other official organizations were involved in the interconnection of networks, such as ITU-T and ISO. They all tried to define a set of protocols, distributed in a well-defined set of layers, so that applications could communicate with each other, regardless of the underlying network technology and operating system on which each application was running
Internetworking
The original designers of the ARPANET protocol stack, subsidized by DARPA (Defense Advanced Research Projects Agency) introduced fundamental concepts such as layer structure and virtuality into the network world, well before ISO was interested
The official body of these researchers was the networked working group called ARPANET, which had its last general meeting in October 1971. DARPA has continued its research in search of a stack of network protocols, from the host-to-host NCP (Network Control Program) protocol to the TCP-IP protocol stack, which took the form it currently has from 1978
At the time, DARPA was an organism famous for pioneering packet switching over radio networks and satellite channels. The first actual implementation of the Internet occurred in 1980, when DARPA began converting machines from its working network (ARPANET) to the new TCP-IP protocols. In 1983 the transition was complete and DARPA demanded that all computers that wanted to connect to ARPANET use TCP-IP
DARPA also hired Bolt, Beranek, and Newman (BNN) to develop an implementation of the Berkeley UNIX TCP-IP protocols on VAX and provided the University of California, Berkeley to distribute that code free of charge with its UNIX operating system. The first release of the Berkeley system distribution that included the TCP-IP protocol was available in 1983 (BSD 4.2)
Since then, TCP-IP has spread rapidly among universities and research centres and has become the standard for UNIX-based communication subsystems. The second release (BSD 4.3) was distributed in 1986, which was updated in 1988 (BSD 4.3 Tahoe) and in 1990 (BSD 4.3 Reno). BSD 4.4 was distributed in 1993. Due to funding constraints, BSD 4.4 will be the latest distribution to be made by the Computer Systems Research Group at the University of California, Berkeley
As TCP-IP spread rapidly, new WANs were created and joined arpaNET in the United States. On the other hand, networks of other types, not necessarily based on TCP-IP, were added to the set of interconnected networks. The result was what is now known as the Internet
Internet
The word Internet is simply a contraction of the phrase interconnected network. However, capitalized refers to a global set of interconnected networks, so that the Internet is an interconnected network, but not the other way around. The Internet is sometimes called Connected Internet
The Internet consists of the following groups of networks:
- Stem
Large networks that exist mainly to interconnect other networks. Currently the trunk networks are NSFNET in the US, EBONE in Europe and the large commercial trunk networks
Regional networks that connect, for example, universities and colleges - Commercial networks
They provide access to trunks and subscribers, and networks owned by commercial organizations for internal use that also have an Internet connection - Local networks
For example, university campus-level networks
In many cases, particularly in commercial, military, and government networks, traffic between them and the rest of the Internet is restricted (by using firewalls)
To find out if we are connected to the Internet, it is checked by pinging the target host. Ping is a program used to determine whether a host on a network is achievable; implemented on any TCP-IP platform. If the answer is no, then you're not connected. This definition does not necessarily imply that one is completely isolated from the Internet: many systems that would fail in this test have, for example, email gateways to the Internet
In recent years the Internet has grown in size and size at a faster rate than anyone could have anticipated. In particular, more than half of the hosts connected to the Internet today are commercial in nature. This is a conflicting, potential and truly, area with the initial objectives of the Internet, which were to promote and care for the development of open communications between academic and research institutions. However, continued growth in the commercial use of the Internet is inevitable so it will be useful to explain how this evolution is taking place
An important initiative to consider is that of AUP (Acceptable Use Policy). The first of these policies was introduced in 1992 and applies to the use of NSFNET. In the AUP fund it is a commitment "to support research and open education". Under "unacceptable uses" is the prohibition of "use for profit", unless they are included in the General Principle or as an acceptable specific use. However, despite these seemingly restrictive instances, NSFNET has increasingly been used for a wide range of activities, including many of a commercial nature
Apart from the NSFNET AUP, many of the networks connected to NSFNET maintain their own AUPs. Some of them are relatively restrictive in their treatment of commercial activities while others are relatively liberal. The important thing is that UPAs will have to evolve as long as the inevitable commercial growth on the Internet continues
Let us now focus on Internet service providers that have developed the most activity in the introduction of commercial uses of the Internet. Two worth mentioning are PSINet and UUNET, which in the late 1980s began offering Internet access to both businesses and individuals
CERFnet, based in California, offers services free of any AUP. Shortly the next, an organization was formed to join PSINet, UUNet, and CERFNet, called CIX (Commercial Internet Exchange). To date, CIX has more than 20 members connecting constituent networks in an AUPs-free environment. Around the same time CIX, a non-profit company, ANS (Advance Network and Services), emerged, it was formed by IBM, MCI and Merit, Inc. In order to operate T1 trunk connections for NSFNT. This group has remained active and increasing its commercial presence on the Internet
ANS also formed a commercially oriented subsidiary called ANS CO+RE to provide links between commercial clients and educational and research domains. ANS CO+RE also provides AUPs-free access to NSFNET when connected to CIX
ARPANET
ARPANET was built by DARPA (called ARPA at the time) in the late 1960s to facilitate the installation of packet switching technology research equipment and to allow resources sharing to Department of Defense contractors. The network interconnected research centres, some military bases and government sites. It soon became popular with researchers by collaborating through email and other services. It was developed oriented to a usefulness for research, used by the DCA (Defense Communications Agency) in late 1975 was divided in 1983 into MILNET, for the interconnection of military locations, and ARPANET, for the interconnection of research centers. This was the first step towards the capital I of the Internet
In 1974, ARPANET was based on 56 kbps leased lines that interconnected packet switching nodes (PSNs) scattered throughout the US and western Europe. They were minicomputers that executed a protocol known as 1822 (by the report number that described it) and dedicated to the packet switching task. Each PSN had at least two connections to other PSNs (to allow alternate routing in the event of a circuit failure) and up to 22 ports for user computer connections (hosts)
1822 systems enable reliable, flow-controlled delivery of a packet to the destination node. This is why the original NCP protocol was a fairly simple protocol. It was replaced by TCP-IP protocols, which do not assume the reliability of the underlying network hardware and can be used in networks other than those based on 1822. The 1822 did not become an industry standard, so DARPA subsequently decided to replace the 1822's packet switching technology with the CCITT X.25 standard
Data traffic soon exceeded the capacity of 56 Kbps lines that constituted the network, which were no longer able to support the required flow. Today ARPANET has been replaced by new trunk technologies in the area of Internet Research (NSFNET), while MILNET remains the backsped web in the military area
NSFNET
NSFNET (National Science Foundation Network) is a three-tier network located in the United States that consists of:
- A backbone
A network that connects separately managed and operated mid-tier networks and NSF-based supercomputer centers. This trunk also has transcontinental links with other networks such as EBONE, the European IP trunk network - Networks of middle-level
- Regional
- Based in a discipline
- Networks formed by a consortium of supercomputers
- Campus networking
Both academic and commercial, connected to mid-level
The first backbone
Originally established by the NSF (National Science Foundation) as a communications network for researchers and scientists to access NSF supercomputers, the first NSFNET trunk used six LSI/11 DEC microcomputers as packet switches, interconnected by 56 Kbps leased lines. There was a primary interconnection between the NSFNET trunk and ARPANET at Carnegie Mellon, which allowed datagram routing between users connected to those networks
The second trunk
The need for a new trunk manifested itself in 1987, when the former became overburdened in a few months (estimated growth at the time was 100% per annum). NSF and MERIT, Inc., a consortium of computer networks from eight Michigan state universities, agreed to develop and manage a new high-speed trunk with greater transmission and switching capabilities
To manage it they defined the IS (Information Services) that is composed of the Information Center and the Technical Support Group. The Information Center is responsible for distributing information, information resource management and electronic communication. The support group provides technical support directly on the field of work. The purpose of this is to provide an integrated information system with easy-to-use and manage interfaces, accessible from anywhere on the network and supported by a range of training services
MERIT and NSF led this project with IBM and MCI. IBM provided software, packet switching equipment, and network management, while MCI provided infrastructure for long-distance transport
Installed in 1988, the new network initially used 448 Kbps leased circuits to interconnect 13 IBM-supplied nodal switching systems (NSSs). Each NSS consisted of nine IBM RT systems (using an IBM version of BSD 4.3) connected through two IBM ring networks (for redundancy). An IBM IDNX (Integrated Digital Network Exchange) was installed in each of the 13 locations to enable:
- Routing, dynamic alternative
- Reservation dynamic bandwidth
The third trunk
In 1989, the topology of NSFNET circuits was reconfigured after having measured traffic and the speed of leased lines was increased to T1 (1,544 Mbps) using mainly fiber optic
Debido a la necesidad constantemente creciente de mejoras en la conmutación de paquetes y en la transmisión, se añadieron tres NSSs a la troncal y se actualizó la velocidad de las conexiones. La migración de NFSNET de T1 a T3 (45 Mbps) se completo a finales de 1992. Advanced Network & Services, Inc. (compañía fundada por IBM, MCI, Merit, Inc.) es en la actualidad el organismo proveedor y gestor de NSFNET
EBONE
EBONE (Pan-European Multi-Protocol Backbone) plays the same role as NSFNET in the US in Internet traffic in Europe. EBONE has connections at kilobit and megabit level between five large centers
CREN
Completed in October 1989, the fusion body of the two famous CSNET (Computer Science Network) and BITNET (Because It's Time Network) formed the CREN (Corporation for Research and Educational Networking). CREN encompasses the CSNET and BITNET family of historical services to provide a rich variety of networking options:
- PhoneNet
It is CSNET's original network service and provides store-and-forward email service using dial telephone lines (1200/2400 bps). It allows users to exchange messages with other members of cren and other large mail networks, including NSFNET, MILNET, etc. - X. 25 Net
It is an Internet-connected CSNET network that provides a full service, using TCP-IP over X.25 protocol. It is common for international members to connect to CSNET because they can use their public data network X.25 to reach Telnet in the US. Provides file transfer, telnet, as well as immediate email service between X.25 Net host - IP of marking
It is an implementation of SLIP (Serial Line IP) that allows sites that use the switched telephone network (9600 bps) to send IP packets, via a central server, to the Internet. Users of this method have the same services as in X.25 Net - IP line leased
Used by many CREN members to connect to CREN. Supports a number of link speeds up to T1 rates - RSCS / NJE sobre BISYNC
It traditionally works on leased lines at 9600 bps and provides interactive message service, unsolicited file transfers and email - RSCS-over-IP
Allows BITNET service hubs to relax dedicated RSCS BYSYNC lines in favor of an IP route, if any
CYPRESS
CYPRESS is a network over leased lines that allows to have a low-cost, protocol-independent packet switching system, mainly used to interconnect small sites to Internet networks over TCP-IP. Established at source as part of a joint research project with CSNET, it is now independent of CSNET
There are no restrictions on its use, other than those imposed by other networks. In this way commercial traffic can pass between two industrial sites through CYPRESS. Industrial sites cannot pass commercial traffic over the Internet due to restrictions imposed by government agencies that control backshed networks (e.g. NSFNET)
TWN
TWN (Terrestrial Wideband Network) is a WAN for the purpose of providing a platform for research with protocols and applications on high-speed networks (paper initially represented by ARPANET). This system includes both connection-oriented and non-connection-oriented services, broadcast and real-time conferencing
The TWN was built and commissioned by BNN Systems and Technologies Corporation during the first half of 1989 as part of the initial phase of the DRI (Defense Research Internet). Its main purpose was to transport throughout the country the traffic of datagrams associated with projects subsidized by DARPA. It was composed of Internet gateways and Terrestrial Wideband Network packet switches (WPSs) that communicated with each other using the Host Access Protocol (HAP) specified in RFC 1221
The WB-MON (Wideband Monitoring Protocol) was used between the WPSs and the monitoring center. The trunk also supported a research environment for multimedia conferencing and speech and video conferencing using gateways that used a real-time connection-oriented protocol (ST-II – Stream Protocol – RFC 1190) over a non-connection-oriented network
EARN (European Academic Research Network)
EARN, launched in 1983, was the first and largest network to serve academic and research institutions in Europe, the Middle East and Africa. EARN began its journey with the help of IBM. It evolved into a non-profit, non-commercial traffic-based network that serves academic and research institutions
RARE (Réseaux Associés pour la Recerche)
RARE, founded in 1986, is the association of European network organizations and their users. The association has 20 FNM (Full National Members; all European countries), numerous ASNs (Associate National Members; some European and Asian countries), IM (International Members; e.g. EARN) and LM (Liason Members; e.g. CREN)
Supports the principles of open systems as defined in ISO in addition to a number of mainly European groups, such as EWOS (European Workshop for Open Systems) and ETSI (European Telecommunications Standards Institute)
RIPE (Réseaux IP Européens)
RIPE coordinates TCP-IP networks for the scientific community in Europe. It operates under the auspices of RARE. RIPE has been in place since 1989. In the early 1990s more than 60 organizations participated in this work. The objective of RIPE is to ensure the administrative and technical coordination necessary to enable the operation of the pan-European IP network. RIPE does not manage any network you own. RIPE can be defined as RARE's IP activity
One of ripe's activities is to maintain a database of European IP networks, DNS domains and their contacts. The content of this database is considered to be in the public domain
Internet in Japan
Japan has many different networks. The following are some of the main ones:
- Japanese BITNET began operating in 1985. It was founded by Tokyo University of Science and part of its members. This network connects to CUNY (City University of New York) via a link to 56 Kbps
- N-1net is managed by the NACSIS (National Center for Science and Information Systems), a research institute founded by the Japanese Ministry of Education. It began operating in 1980 using an X.25 packet switching network. N-1net has a 50 Kbps connection to the NSF in Washington
- Todai's TISN (International Science Network) is used by physicists and chemists. TISN has a 128 Kbps link between Todai and Hawaii
- WIDE (Widely Integrated Distributed Environment) is the Japanese version of the Internet. It began as a research project in 1986. There are two connections between WIDE and the rest of the Internet. One, 192 Kbps, goes from Keio University in Fujisawa to the University of Hawaii. The other is a 128 Kbps secondary link from Todai to Hawaii, provided for in the event that the main