Cryptography
The history of cryptography is long. Since the first civilizations developed techniques to send messages during military campaigns, so that if the messenger was intercepted the information that he had not run the danger of falling into the hands of the enemy
Since the times of Ancient Egypt up to today has been a long time, but there is something that has not changed: the desire of the human being by hiding their secrets
Ancient
Characters such as Cleopatra or Caesar already learned to appreciate the importance to hide from prying eyes your messages. The Scilata that the spartans used back in the year 400 B. C. or the own code Caesar (a simple scroll alphabetically) were the beginnings
With the development of the sciences, and, more specifically, of mathematics, cryptography grew up as a younger brother, hand in hand. In the Middle Ages began to acquire a great importance when a servant of Pope Clement VII wrote the first manual on the topic of the story in the old continent
In 1466 Leon Battista Alberti devised the system polyalphabetic based on the rotation of a roller. A century later, Giovanni Battista Belaso invents the cryptographic key based on a word or text that you are transcribing letter by letter on the original message
The Twentieth century
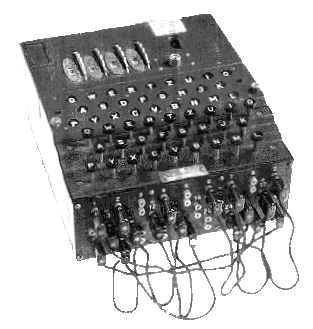
Already at the beginning of the last Twentieth century devised the denominated “translators mechanics”, based on the concept devised in the XV century by Alberti of the wheels concentric, and the system began to become extremely complex, since it is not enough to analyze it thoroughly to understand it. And that led to the Second World War, to the years 30 and 40 and to the Enigma machine
Although a lot of people don't know, the cryptography was one of the main reasons for the allies to win the war, because the germans believed the code of their Enigma machine as inviolable, and in fact yes that was extremely complex. But like before I said that the human desire to hide secrets is eternal, so is his longing for unearthing other people's secrets
A team of criptoanalistas, mathematicians, and other minds, the privileged (among them Alan Mathison Turing, one of the fathers of computer science) won in 1942 what seemed impossible: to break the encryption of Enigma
To do so, they designed the so-called “bombs naval” (la bombe de Turing), equipment of calculation mechanics who were in charge of breaking the German encryption and deliver all the secrets to the allies
Also, the Purple (japanese version of Enigma) was broken Midway by a team led by commander Joseph J. Rochefort. The fact that you know the secrets, you have all the keys (never better said), turned the war and changed the course of history. And the world will never again be the same
Cryptography today
The birth of computers and the cryptosystems computer was a radical change of the concept of cryptography, and cryptanalysis. The cryptosystems and algorithms increased suddenly and unwieldy complexity
From the DES a long time ago, until the cryptosystems asymmetric elliptic curves today everything has changed too much, but one of those changes has been the second major turning point of cryptography: PGP
Until then, the privilege of keeping secrets was exclusively in the hands of the governments or the powerful, and today, probably thanks to PGP, is a right of any citizen by humble (although in some countries is not so). Risking much, Arthur Zimmermann we opened the doors to the cryptography, and the freedom to communicate safely
Of course there are other names that are capital in the development of cryptosystems computer, apart from Zimmermann: Rivest, Shamir, Adleman, Diffie, Hellman, ElGamal, Rijmen, Daemen, Massey, Miller, Goldwaser... they are All fathers of what today is called cryptography
Basic concepts
Cryptology
Cryptography art of hide. The word has its origin in the Greek: kryptos (hidden, hidden) and graphein (to write). The art of concealing a message by means of conventional signs is very old, almost as much as the writing
And effectively has always been considered an art until relatively recently, when Claude Elwood Shannon published in two years, two documents that constituted the foundation of modern Information Theory. These documents are:
- A mathematical theory of communication
- Communication theory of secrecy systems
Cryptography the art of writing with a secret key or in an enigmatic manner
Cryptanalysis art of deciphering cryptograms
Clear text and cryptograms
In the area of cryptographic, we understand by clear text any information that is readable and understandable per se. A clear text would be any information before being encrypted or after being decrypted. It is considered that any information is vulnerable if you are in this state
Likewise, we call cryptogram any information that is suitably encrypted and will not be readable or understandable for the rightful recipient of the same
The mechanism of transforming a plain text into a cipher, what we call encryption or encryptionand the process of retrieval of information from a cryptogram we call decryption or decryption
It is very important not to confuse these terms with encoding or decoding
Encoding is the act of representing information in different ways, but not necessarily encrypted. For example, a decimal number may be encoded as hexadecimal, and turns into a cryptogram
Flow of information
In a cryptosystem, the information continues to flow is always fixed:

The sender encrypts the plain text to obtain the cryptogram, which travels through a channel noisy. The receiver decrypts the cipher, and again obtains the plain text that the sender sent him. During the transmission, the message is unreadable
Cryptosystems
First of all, it is convenient to define what we mean “mathematically” by cryptosystem. A cryptosystem is a quarternary of elements formed by:
- A finite set called the alphabet, which according to rules of syntax and semantics, allows to emit a message in clear as well as its corresponding cryptogram
- A finite set called the key space formed by all the possible keys both for encryption as for decryption, the cryptosystem
- A family of applications in the alphabet in itself, which we call transformations of encryption
- A family of applications in the alphabet in itself, which we call transformations of decryption
We already know what is a cryptosystem, but what is a cryptosystem computer? A cryptosystem computer would be defined by the following four elements:
- A finite set called the alphabet, which allows to represent both the clear text as the verification value. At low level we would speak of bitsand at a higher level we could speak of the characters ASCII or MIME
- A finite set called the key space. Would be constituted by all the possible keys of the cryptosystem
- A family of transformations, arithmetic-logic, which we call transformations of encryption
- A family of transformations, arithmetic-logic, which we call transformations of decryption
It is simply a cryptosystem adapted to the possibilities and limitations of a machine. The alphabet or space characters is usually a standard representation of information (typically MIME or UNICODE for compatibility reasons) and the lowest level, by bit. The transformations of both encryption and decryption follow the rules of programming computers today
In reality, for all practical purposes there is not much difference between cryptosystem mathematical and computer, since mathematicians tend to design thinking in their programming in a machine (because only computers have the power necessary to support the complex algorithms) and the software is developed always with a mathematical basis
Cryptographic algorithm
A algorithm you must describe uniquely and without giving rise to interpretations, the solution to a problem in a finite number of steps concrete
Encryption algorithm, is a description clear and specific of how a cryptosystem given
Cryptographic key
The concept of a cryptographic key that arises with the concept of cryptography, and is the soul of an encryption algorithm
Obviously, an algorithm must possess the ability to be worn many times without that its mechanism is identical, because, otherwise, each person should have their own encryption algorithm
To implement this functionality, use the keys. The key it is a data it intervenes actively in the implementation of the algorithm and customizes it
Solely to the type of key, we can distinguish between two cryptosystems:
- Systems or unique key cryptosystems, symmetric
Are those in which the encryption and decryption processes are carried out by a single key - Of public key systems or cryptosystems asymmetric
Are those in which the encryption and decryption processes are carried out by two different keys, and complementary
Key length
Today, thanks to computers it is possible to perform complex mathematical computations in a space of relatively short time. Thus, the field of cryptanalysis is closely linked to this computing power
For that an algorithm is considered secure, his cryptanalysis without the required key should be computationally impossible to solve
We consider it “impossible” to solve a system whose violations need greater resources (financial or time) that the benefit reported. For example, it is considered secure a cryptosystem that requires thousands of years for decryption
To achieve such a complexity, address numbers or sets of numbers huge. It is obvious that the greater the size of these numbers, there is a greater number of possible keys, and the possibility of success of the cryptanalysis is less
Today this size is called the key length, and is typically measured in the bit that holds the key. So, a key number of 1024-bit would be any number from 0 up to the 1,8\cdot 10^{308} (2^{1024})
By representing the key lengths as powers of two, it is important to realize the relationship between the lengths of key. A key 1025 bits is the double of long that a 1024 - (2^{1025} front 2^{1024})
Today use keys ranging from 512 bits and 4096 bits in length