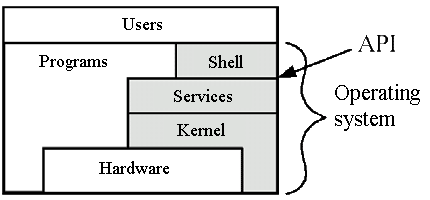
Operating system
An operating system is a set of programs that, by providing abstractions, they put the hardware of the machine available to users in a safe and effective
Objectives of an operating system:
- To simplify the use of the machine
- To make efficient use of the resources of the machine
- Control the execution of application programs
Functions of the operating system
The operating system as user interface:
- Interpreter command or shell (text or graphics)
- Files commands or shell scripts
The operating system as resources manager (Resolves competition for resources):
- Allocation and recovery of resources
- Protection between users
- Accounting and monitoring
The operating system as a virtual machine. Offers services to the user processes via a set of functions (system calls) that make up its application programming interface (API):
- Creation of processes/threads for the execution of programs
- Orders of input/output (I/O)
- Operations on files
- Detection and treatment of errors in the operating system itself
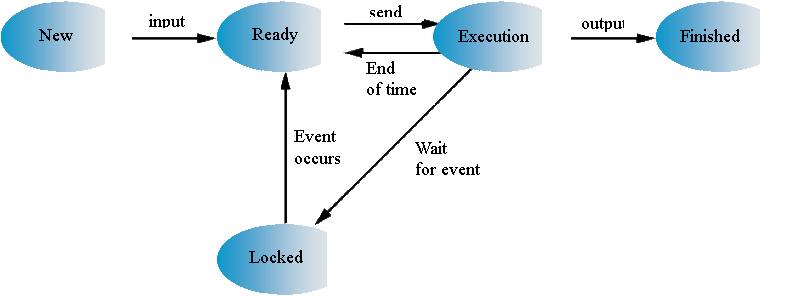
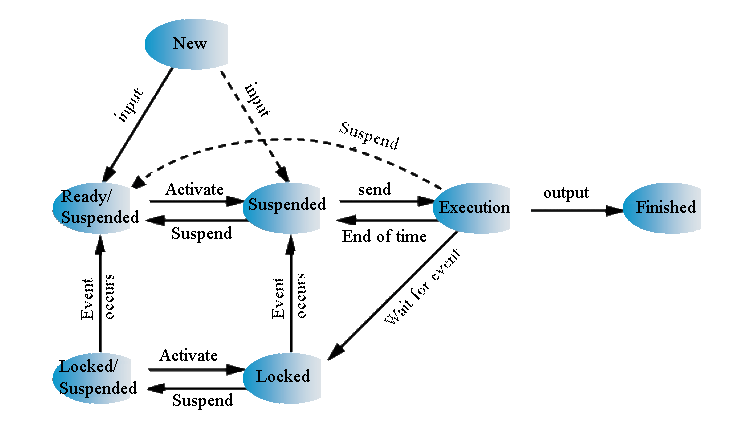
Multiprogramación and time-sharing
Depending on the number of processes and users that may run concurrently, an operating system can be:
- Monotarea or monoproceso
- Multi-tasking, multi-threaded or multiprogramación
- Objective: maximize the utilization of the processor
- Single-user
- Multi-user or time-sharing
- Goal: minimize response time
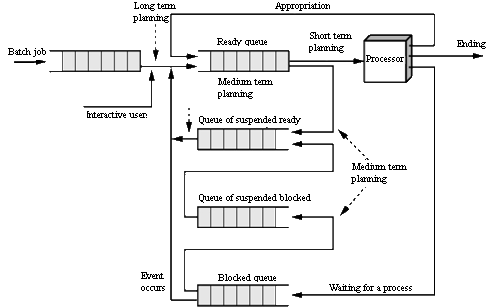
When a process needs to wait for an I/O statement, the processor can switch to a different process, this will get the multiprogramación
For that to be possible:
- There must be a memory management to divide the main memory among multiple processes
- Sharing multiplexed in space
- There must be a planning to distribute the CPU time among the processes that are in memory
- Sharing multiplexed in time
- There must be protection mechanisms for the shared use of resources
- The operating system allocates the devices to the processes and provides the I/O routines
Architecture Von Neumann
The architecture Von Neumann model (Von Neumann architecture or Princeton), is an architecture for computers based on that described in 1945 by the mathematician and physicist John von Neumann and others, first draft of a report on the EDVAC (Electronic Discrete Variable Automatic Computer)
Describes the architecture for the design of a digital computer electronic parts which consist of a processing unit that contains a unit arithmetic logic and processor registers, a control unit, which contains a record of instructions and a program counter, a memory to store both data and instructions, external mass-storage, and mechanisms for input and output
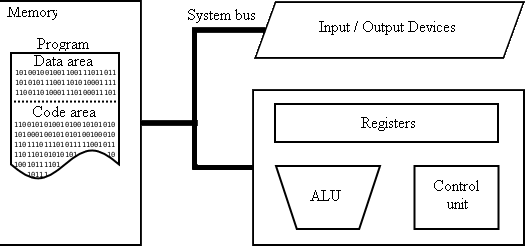
Processor registers
Program counter (CP)
Holds the address of the main memory of the next instruction that you have to load the control unit
Instruction register (IR)
Contains a copy of the current statement, obtained from the main memory
The process hardware
Sequence of read-and-running:
- Read the instruction pointed by the program counter (CP)
- Increase in the CP
- Execution of the instruction, A computer only knows how to repeat it at great speed this sequence
You can break this linear sequence by modifying the value of the CP by:
- Machine instructions jump
- Interruptions internal interruptions)
- External interrupts (exceptions)
- Instruction trap (trap)
External interrupts
Commonly known as disruptions
An interrupt is a signal received by the CPU, indicating that it must interrupt its normal execution and to happen to execute specific code to treat this situation
It is the mechanism used by devices to request attention from the CPU:
- Periodic interrupts of watch
- Interruptions of the I/O devices
Treatment of interruptions
Hardware, cycle of acceptance of interruption:
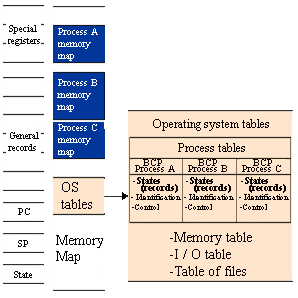
- Saves the context of the running process
- Content of some processor registers
- Raises the level of execution of the processor (by passing it to kernel mode)
- Load a new value in the pc (jumps to the operating system)
For software, the operating system executes a routine treatment of the interruption
Interrupts internal
Also called exceptions, are unexpected events internal to the processor:
- Arithmetic overflow
- Division by zero
- Invalid address
- Attempt to execute a privileged instruction
Treatment of the exceptions
The management of exceptions is similar to that of the interruptions. Upon detection of the exception, transferring control to the handler of exceptions.The basic difference with the interruptions is that the exceptions tend to be handled in the user space. The operating system only notifies
Instruction trap (trap)
A user process performs a privileged operation by the instruction trap
Is an instruction in user mode generates an exception
Some call it disruption software, or also, call the supervisor (SVC)
It is invoked by a process that is running in user mode and you want to perform an operation that requires privileged instructions
Change the bit mode and branches to a fixed position of the space of the system
Dual-mode execution of the CPU
We call privileged instructions to those machine instructions that can potentially affect other processes:
- I/O operations
- Update the clock
- Disable interrupts
Controlling the execution of privileged instructions we protect other processes and the operating system
Solution: To distinguish the two execution modes of the CPU
The processors now include a bit of mode that modifies the level of execution:
- User mode
- You can only run instructions are not privileged
- The process only accesses to the user space
- Supervisor mode or kernel
- It can run any instruction
- Is called a kernel (or kernel) of the operating system code that runs in this mode
- Only the code of the operating system can run in supervisor mode and has access to both the system space as the user
Conclusion: The trusted software of the operating system runs in supervisor mode and the rest of the software runs in user mode
System calls
The system calls are procedures or functions provided by the operating system
Allow user processes to perform privileged operations
They are implemented through the instruction trap
- The instruction trap is in need of an operand to reference a table from the core table (trap)
To hide the details of the instruction trap, the designer of the operating system provides a library of functions of “shelter”
- The names of the functions guard coincide with those of the system calls
- Each shelter contains an instruction to trap to the operating system function through the correct entry of the table of the trap to the kernel
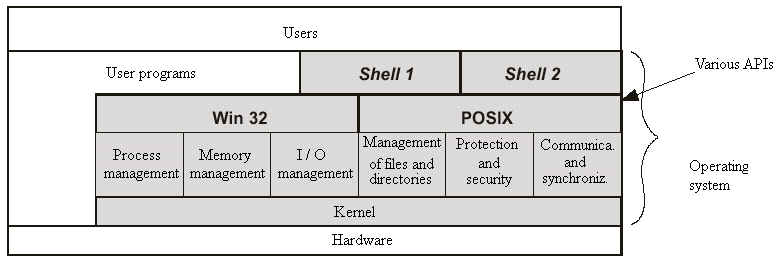
Interface of system calls
Each operating system implements its own set of system calls that are exported through a call interface
This set of calls is the interface of the operating system with the application program or API (Application Program Interface)
The application programs invoke operating system services by calling the functions defined in the interface of system calls
The functions are implemented by various parts of the operating system: process manager, memory manager, device manager and file manager
Examples:
- API standard POSIX on UNIX and Linux
- Win32 API on Windows
POSIX
Standard interface operating system portable IEEE based on UNIX
Goal: portability of applications between different platforms and operating systems
It is not a deployment. Only defines a specification
Available in all versions of UNIX and Linux
Windows 2000 offers a subsystem of POSIX
Features
Function names short and in lowercase
- fork
- read
- close
The functions normally return 0 if successfully executed, or -1 in case of error
- Variable errno
Most of the resources managed by the operating system are referred to by descriptors: whole number greater than or equal to zero
Win32
It is not a standard
It is an API totally different from the POSIX standard
Defines the services offered by the systems Windows 95/98, Windows NT, Windows 2000 and Windows XP
It defines functions and graphic services
Features
Name of the functions long and descriptive
- GetFileAttributes
- CreateNamedPipe
It has predefined data types
- BOOL
- DWORD
- TCHAR
The functions return, in general, true if the call was executed successfully or false otherwise
The resources are managed as objects,referenced by handlers
Design of the internal structure of the operating system
Monitor monolithic
All the operating system is designed as a single module composed by functions that can call each other
The user processes and the I/O devices communicate through the core
When code is executed by the monitor interrupts are disabled
Examples: MS-DOS, Windows XP, UNIX, Linux
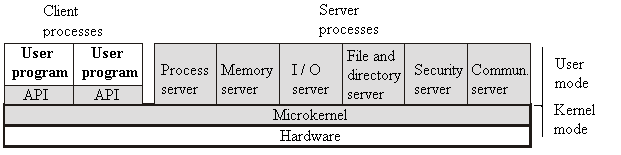
Microkernel
Some of the functions of the operating system are implemented as server processes in user
The kernel functions are reduced to a minimum, so that the reliability of the system increases
Examples: Minix, Mach, Windows NT