Protocol
A protocol is a set of rules and conventions for sending information over a network
Protocols supported by Windows and GNU/Linux include TCP/IP, which is used for login, printing services, copying information between domain controllers, and other common functions
We also have the following protocols for Windows:
- Asynchronous Transfer Mode (ATM)
- LAN emulation
- IP over ATM
- ATM over xDSL
- Native ATM access through Winsock 2.0
- Internet Packet Exchange/Interwork Packet Exchange (IPX/SPX)
- NetBEUI Enhanced User Interface (NetBEUI)
- AppleTalk
- Data Link Control (DLC)
- Infrared Data Association (IrDA)
Binding order of the protocols
Protocols can be added and deleted at will and selectively bound to all network interfaces that exist on the server. The binding order of the protocols is determined by the order in which they were installed in principle, although it can be changed at any time, interface by interface, allowing a greater degree of control. For example, the first interface might have TCP/IP and IPX/SPX bindings, taking TCP/IP precedence, while the second interface might still have both protocols bound while preceding the IPX/SPX protocol. Additionally, network services can be selectively turned on or off by adapter or protocol or any combination there. This selectivity gives system administrators very good control over network connection settings and allows very secure configurations (such as disabling all network services on all public interfaces directly connected to the Internet) to be built with minimal difficulty
Protocols
ATM
Asynchronous Transfer Mode Protocol (ATM) is an advanced implementation of packet switching that is ideal for voice, video, and data communications. ATM is a high-speed technology for network work that transmits data in cells of a fixed size. It consists of a number of technologies including software, hardware and connection-oriented media
A cell is a fixed-size package that contains 53 bytes of information, as shown in the figure:
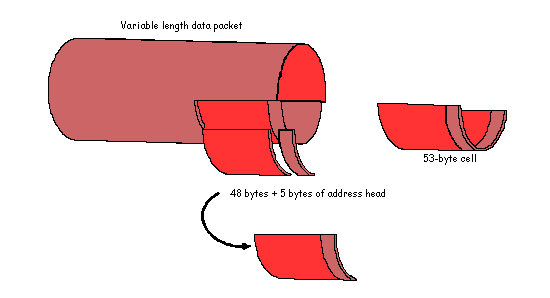
Because the number of bytes, and consequently the transmission time, of a cell is constant, cells can be switched over a constant interval
An ATM endpoint establishes a connection or virtual circuit before sending any data over the network. Then send the cells through this path to the destination. This virtual circuit is a direct path from one end to the other. While the connection is established, the ATM endpoint negotiates a Quality of Service (QoS) contract for transmission. This contract explains the bandwidth, maximum delay, acceptable variation, and other parameters provided by the virtual circuit (VC) that extend end-to-end. Because the virtual circuit is connection-oriented, data reaches the source destination endpoint and with the specified service levels, ATM is an excellent compromise for both voice and data transmission over a network. ATM provides guaranteed QoS on a local area network (LAN), a wide area network (WAN), and a public inter-network
LANE
LANE (LAN Emulation) is a method by which protocols that only understand offline media can communicate over ATM. This allows ATM to use both legacy networks and legacy applications. Applications and protocols for traditional local networks can be communicated without modification over an ATM network
LANE consists of two main components: the LANE client (Atmlane.sys) and LANE services
The LANE client on Windows is located in the folder %systemroot%\system32\drivers. This allows LAN protocols and on-premises applications to function as if they were communicating with a traditional LAN. Lane client communicates LAN commands to network protocols and native ATM commands to ATM protocol layer
LANE services are a group of ATM components, typically located on a switch that supports LAN emulation
Ip over ATM
IP over ATM is a group of services that are used for communications over an ATM network and can be used as an alternative to ATM emulation. IP over ATM uses ATM connection orientation properties to overcome the offline nature of IP. It works similarly to LANE. A central IP server (called an ATMARP server) maintains an IP address database and ATM provides configuration and broadcast services. These broadcast services are necessary because ATM is a non-broadcast protocol. IP over ATM services are not located in a single site and are typically not on an ATM switch. All IP over ATM services are provided with Windows
In fact, IP over ATM is a small layer found in ATM protocol and TCP/IP protocols. The client emulates, in its upper margin, the standard IP for the TCP/IP protocol, and below uses native ATM commands for ATM protocol layers
IP over ATM is handled by two main components: the Address Resolution Protocol (ARP) server (Atmarps.sys) and the ARP client (Atmarpc.sys)
The ARP server consists of an ATMARP server and a multicast address resolution (MARS) service. The ATMARP service provides services that emulate standard IP functions, while MARS provides broadcast and multicast services. Both services maintain IP address databases
ATM over xDSL
xDSL (Digital Subscriber Line) is a means by which POTS (plain old telephone service) can be used to send digital data to a central station of a telephony company using a pair of copper cables. To connect many DSL users to an ATM-supported network, DSL data is sent to a DSLAM (Digital Subscriber Line Access Multiplexer). On the opposite side of DSLAM, it connects to an ATM network that provides gigabit order data rates. On the other side of each transmission, a DSLAM demultiplexes the signals and directs to the appropriate individual DSL connections
ATM over xDSL provides access to high-speed networks from home and small office environments. Many types of DSL, including ADSL (asymmetric digital subscriber line) and VDSL (very high digital subscriber line), are developed in these areas. These technologies use the local loop, copper cable for ADSL, or fiber optics for VDSL, which connects the local head office to the user data connector in a user environment. In many areas, this local loop connects directly to an ATM-core network provided by a telephony company
The ATM over xDSL service presents the high-speed features and QoS guarantees available on the ATM core network without changing protocols. This creates the potential for a point-to-point ATM network for home and small offices
Native ATM access through Winsock 2.0
ATM support for Winsock 2.0 is available through the Windows Sockets ATM service provider. As a result, applications that use TCP as their transport protocol can directly use Winsock 2.0 to access ATM/ip-based networks
Applications that use native ATM can create virtual circuits and access QoS guarantees. This capability is provided through a connection-oriented service added to Version 5.0 of the Network Driver Interface Service (NDIS). The connection-oriented service in NDIS 5.0 is called CoNDIS
NWLink
NWLink is Microsoft's implementation of Novell Netware's IPX/SPX protocol. NWLink is typically used in environments where clients operate under Microsoft operating systems to access NetWare resources or where client computers operate under Windows and run NetWare to access resources. NWLink does not allow direct access to shared files or printers on a NetWare server. NWLink must be used to access files or printers on a NetWare server, such as CSNW (Client Service for NetWare) in Windows Professional or GSNW (Gateway Service for NetWare) on Windows Server
GSNW acts as a re-consigte on Windows Server computers and as a gateway for client computers. The gateway feature allows a Windows Server computer to share NetWare resources (folders and printers) as if they were located on Windows itself. As a result, client computers that are able to access shares on the Windows Server computer can use the shares that have been made available through GSNW. GSNW is a low-performance access solution; allows a single-user connection to provide gateway access to resources on a NetWare server
NWLink is useful if there are Client/Server NetWare applications running that use Winsock or NetBIOS protocols over IPX/SPX. Additionally, NWNBLink (NetWare NetBIOS Link) contains Microsoft enhancements for NetBIOS. The NWNBLink element is used to format NetBIOS-level requests and pass them to the NWNBLink element for transmission over the network
Frame type
The frame type defines how a network adapter, on a Windows computer, formats data for send over a network. NWLink needs to be configured on the Windows computer with the same frame type that NetWare servers use to communicate with each other the Windows computer and NetWar servers
The following table lists the topologies and frame types that NWLink supports:
| Topology | Frame type supported |
| Ethernet | Ethernet II, 802.3, 802.2, and SNAP (Sub NetWork Access Protocol) which defaults to 802.2 |
| Token ring | 802.5 and SNAP |
| FDDI (Fiber Distributed Data Interface) | 802.2 and 802.3 |
On Ethernet networks, 802.3 is the standard frame type for NetWare 2.2 and NetWare 3.11. starting with NetWare 3.12, the default frame type changed to 802.2
You can choose to automatically detect the frame type or configure it manually. However, the frame type is automatically detected when NWLink is loaded. If multiple frame types are detected in addition to frame type 802.2, NWLink defaults to frame type 802.2
If the frame type is manually configured, a Windows computer can simultaneously use multiple frame types
You can configure the frame type using the NWLink IPX/NetBIOS Compliant Transport Protocol Properties dialog box (NWLink IPX/SPX/NetBIOS-Compatible Transport Protocol Propities)
NetBEUI
NetBEUI was originally developed as a protocol for small department LANs of between 20 and 200 computers. NetBEUI is not routable because it does not have a network layer. Because of this limitation, Windows and NetBEUI computers should be connected using bridges instead of routers. In addition, NetBEUI is broadcast-based, which means that it relies on broadcasting for many of its functions, such as registration and name discovery, and therefore creates more broadcast traffic than other protocols. NetBEUI is included in Windows Server and Windows Professional as a legacy protocol to support workstations that have not been upgraded from Windows NT
NetBEUI provides support for existing LANs that use the NetBEUI protocol. Providing the following features to Windows computers:
- Communication oriented to connection, and no connection between computers
- Auto-configuration and auto-tuning
- Protection errors
- Little overhead on memory
Note A Windows network running Active Directory services cannot use the NWLink or NetBEUI as its primary protocol. Only TCP/IP is supported to access Active Directory services
AppleTalk
AppleTalk is a family of protocols developed by Apple Computer Corporation for communication between Macintosh computers. Windows includes support for AppleTalk, allowing Windows Server computers and Apple Macintosh clients to share files and printers. AppleTalk also allows Windows to be a router and dial-up service
For the AppleTalk protocol to work properly, a Windows Server computer must be configured with Windows Services for Macintosh and must be available on the network
DLC
The DLC protocol was developed for communication between ibm's large systems. It was not designed to be a network protocol between personal computers. DLC is used to print to Hewlett-Packard printers that connect directly to the network. Network-connected printers use the DLC protocol because the frames they receive are easy to dissociate and because DLC functionality can be easily ROM-encoded (Read Only Memory)
The DLC utility is limited because it does not interact directly with the transport controller interface layer. DLC should only be installed on network machines that perform tasks such as sending data to a network Hewlett-Packard printer. Clients that send print jobs to a network printing device using a Windows print server do not need to have the protocol installed
Only the print server that communicates directly with the print device requires the DLC protocol to be installed. Once the DLC protocol is installed on a Windows Server computer, a new type of print port is available
The MAC (Media Access Control) address of the network adapter card of the available DLC printers or print servers appear in the larger box below the Card Address
Be sure that the DLC enabled network printing device is connected to the network, powered on and configured to work with DLC
After a Windows Server computer has been configured to perform the print server role and DLC-enabled, computers can connect a shared printer to Windows Server. If print jobs appear on the DLC-enabled printing device and are not sent through the Windows Server print server, client computers might be running the DLC protocol and printing directly to the DLC-enabled device. Network Monitor or other network analyzer can be used to determine which computers on the network are running the DLC protocol
Note All Hewlett-Packard JetDirect cards currently support the TCP/IP family and should be added using the standard TCP/IP port. Only older Hewlett-Packard JetDirect cards that do not support TCP/IP need the Hewlett-Packard network port that uses the DLC protocol
IrDA
IrDA is a group of short-range, high-speed, bidirectional wireless infrared protocols. IrDA allows a variety of devices to communicate with each other, such as cameras, printers, laptops, desktops, and PDA (Personal Digital Assistants). IrDA protocol stack accessed using offline NDIS drivers
