Content
- 1 Local area network
- 1.1 Types of communication protocols
- 1.2 Elements of a network
- 1.3 Architecture of area networks to local
- 1.4 Connection of a local network to the Internet
- 1.5 The topology of the local networks
Local area network
LAN (Local Area Network) is a computer network covering a small area of a house, an apartment or a building
The main properties of the local area networks are:
- Include a small physical area. May include an office building, or an office specific to that building, a company, a university
The advantages offered by LANs are:
- Sharing peripherals expensive, as are printers, plotters, scanners, modems, ...
- Share information through the use of database managers in the network. It avoids the redundancy of data and facilitate the access and the update of the data
- The network becomes a mechanism of communication between users connected to it, as it allows the sending of messages through the use of e-mail, either between users of the local network or between users of other networks or computer systems, scheduling meetings or exchanging files of all types
- It increases the efficiency of the computer, giving the user a whole system that makes the queries are faster and more comfortable
- It is a fully secure system, and can prevent certain users from accessing areas of specific information, or they can read the information but not modify it. The access to the network is controlled through user names and access keys. The control of users that access the network carried out by the operating system. The control of the users accessing the information carried out by the software of management of database you are using
Network operating systems try to give the feeling that the remote resources accessed by the user are local to the computer from which you are working the user. For example, a user may be querying information from a database. The user at any time has knowledge of if the information you are accessing is on their own computer or on another within your local network or in any other part of the world
Types of communication protocols
We will list the most appropriate for local networks:
-
Contest
- Contest simple
- Access carrier sense multiple (CSMA)
- Multiple access carrier sense with collision detection (CSMA/CD)
- Sense multiple access carrier-to-avoiding collisions (CSMA/CA)
- With polling (selective call)
- Token-passing (token passing)
Protocols of race
The protocols of race are based on the use of a shared medium with the rule that the first who arrives is the one that uses it
Contest simple
The messages are sent over the shared medium. Computers only respond to messages that include their address. When a team does not send a message, stay on hold listening to the middle, until you receive one with your address
The messages to be transmitted are transformed into packets and sent without looking if the medium is available. When a computer match with the other a collision occurs. The packets that collide are destroyed and the equipment should be forwarded
When a computer receives a packet, it sends acknowledgement of receipt. If a team, after a marked time, you do not receive acknowledgement of receipt, and forwards the packet
Access carrier sense multiple (CSMA)
Before sending information, the computer listen to the line, usually in a secondary frequency, in order to know if another computer is using the main channel of transmission, i.e., the carrier. When the line is free it begins to transmit
There are two methods of waiting:
- Continuous detection of carrier
Listening to the line until it's free - Detection non-continuous carrier
If the line is busy is retried after a period of time marked
When you access the line, the computer transmits two signals, one to indicate that the line is busy, another to transmit the message. Once transmitted, the computer waits for acknowledgement of receipt. Collisions are inevitable because when two teams come at once to the line free, use it, apart from that it takes a long time for the signal to traverse the medium
Multiple access carrier sense with collision detection (CSMA/CD)
In this protocol, in addition to knowing if it is using the medium before starting to transmit, it checks to see if there is a collision, in which case the transmission is interrupted. After a marked time, it restarts the process
Sense multiple access carrier-to-avoiding collisions (CSMA/CA)
When a computer wants to send a message, it checks that the line is free, once confirmed, indicates that you want to convey. If several computers that wish to transmit, the order is determined by a schema already set
Protocols with polling (selective call)
A central computer interrogates a secondary computer on if you want to perform transmission. If yes, authorize the secondary computer to transmit, by assigning a certain amount of time. In negative case it goes to the next secondary computer
The messages can follow one of two paths:
- Pass all by the central team, which forwards it to the secondary computer of destination
- Each team can send messages directly to the destination
The call frequency to the secondary stations, it can vary in function of its priority, its level of activity, etc
Protocols token-passing (token passing)
It continuously circulates a witness or group of bits, so that the computer that has it can transmit
The witness is composed of header, data field and final field. When a team receives a witness empty, and you want to convey inserted in the header address and the destination address, and in the field of data information, and sends it. The maximum length that can be sent is fixed. The following computer picks up the token busy, if not for him, this is what goes on to the next. When it arrives at the recipient this reads it, puts a mark of accepted or denied, and return it to pass
When it comes to the issuer, to be read, delete the message, mark it as empty, and sends it to the next team
Elements of a network
The networks are composed of different types of items, we will give the basic properties of each one of them
HOST
The devices that connect directly to a network segment are referred to as hosts. These include computers, both clients as servers, printers, and various types of user devices
Devices hosts do not form part of any layer of the OSI model. Have physical access to the network via a network card (NIC)
Operating in the 7 layers of the OSI model, running all type of encapsulation to send messages, print reports, etc
The internal operation of a host can be considered as a miniature network, that connects the bus and the expansion slots with the CPU, the RAM and the ROM
NIC
The NIC, or network card corresponds to level two of the OSI model. And provide network access to a computer to the network
Are considered devices of layer two, because each NIC has a name that is hard coded and unique, so-called MAC (Media Access Control). This address is used for the communication of the hosts on the network
In some cases, the type of connector on the NIC does not match with the environment to which it will connect. In this case, it uses a transceiver (transmitter/receiver) that converts the signal from one type to another. Are considered elements of the layer 1
Media
The basic functions of the media consist of transporting a flow of information in form of bits and bytes, through a LAN. Unless the wireless devices that use the atmosphere or space as a means
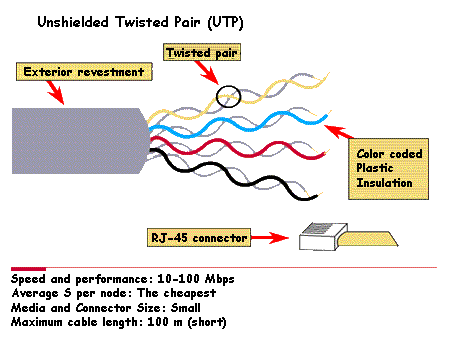
Are elements of the one layer. You can develop networks with different types of media. Each medium has its advantage and disadvantage, considering aspects such as the length of the cable to use, the cost and ease of installation
The most commonly used medium is Category 5 Unshielded Twisted Pair Cable (UTP CAT 5)
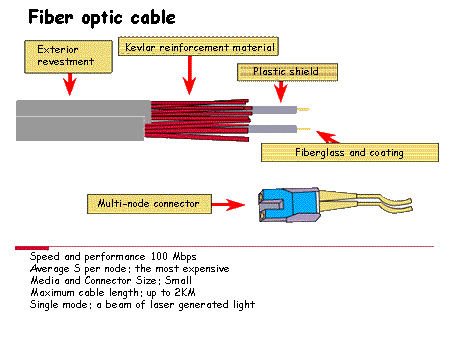
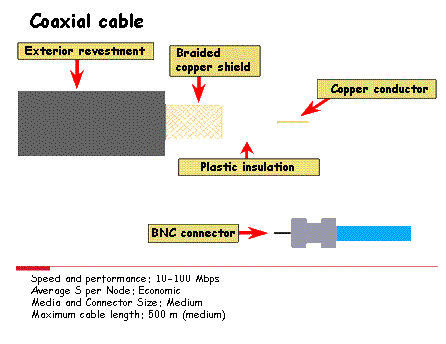
Others also used are the coaxial cable and the fiber optic
Repeaters / HUBs
When you have reached the limit of length of a medium, to use the elements known as repeaters to strengthen the signal, regenerating and retemporizando the same
Are elements of the one layer, since they act only on the bit. Traditionally, it is considered an element with an input and an output, the repeaters of multiple ports is called a HUB
The HUBs connect multiple cables, this increases the reliability, if it fails one of the means connected to it, only to fail that in particular, unlike a bus topology, in which all the elements use the same medium
There are different classifications of HUBs, the first is whether they are assets or liabilities. Currently, almost all of them are active, that is, that need to be connected to the electrical supply to regenerate the signals
Another classification are the HUB intelligent, or not intelligent. The HUB smart have console ports that allow you to program them to manage the network traffic. The not-smart to simply take the signal of the incoming network and repeated to each port, without regard to which
The equivalent of the HUBs in the wireless network are access points (AP)
Bridges
A bridge is a device that is layer two which connects two network segments, filtering traffic to get that local traffic remains local, and at the same time be able to connect with the other segment
The way to carry out this, it is discriminating for a list of MAC addresses that the bridge stores, to discern which are from a network or other
The routers and switches have adopted many of the features of the bridge, but they continue to have great importance in the networks
Switches
A switch is an element of layer two, which is able to know for whom is the information passed by him in every moment, using the frame MAC, and act accordingly, only enviándosela to the interested
This element significantly reduces the collisions that can occur in a same network segment or the same
It is a good item to join small networks, will prevent the information of a network “bother” to other networks
Some switches are highly configurable allowing, for example, create a VLAN to isolate different parts of a network from another
If you can cope up to the price difference, they are preferred over hubs
Routers
The router is a device that is the layer three, therefore this device can make decisions based on groups of network addresses, in contrast to the MAC addresses
The routers can serve to unite different technologies of layer 2. Given its breadth, to route packets based on layer 3, they have become the backbone of the Internet
The purpose of a router is to examine incoming packets (layer data 3), to choose what is the best path for them through the network and then conmutarlos to the output port appropriate
Router by software
To perform the task of router, we can use other elements as may be a computer with multiple network cards
The computer will do the functions of a router by means of the operating system and the installed software, an example of what is needed in a router is implemented in GNU/Linux would be:
- One or more network cards installed and configured properly
- The telnet service to allow remote configuration
- Also the service is Routed, that will allow the routing
- Enable IP_Forward in the kernel of the system
And we only missing, add the appropriate paths
Switches of layer 4 load balancers
Load balancers help to improve the performance of the network by balancing efficiently load one or multiple servers
This device helps to distribute the requests that a server can receive. For example, if we have three web servers, a load balancer will divide the requests between those three servers on the part of customers, in a percentage that you previously configured
With its use, you can avoid overruns by part of a server, and spreads the work efficiently among all
Gateway
Gateway is a device that allows you to connect two networks, usually of a different protocol or a mainframe to a network
Architecture of area networks to local
The offer of local area networks is very wide, and there are solutions for almost any circumstance. We can select the cable type, topology, and even the type of transmission that more suit our needs. However, of all this offer the solutions more widely spread are the following three: Ethernet, Token Ring, and Arcnet
Ethernet (IEEE 802.3)
This network was originally developed by Xerox and Dec as a way of solving the problem of the wiring of networks. Its inventors were Robert Metcalf and David Boggs. According to Robert Metcalfe, the name Ethernet comes from the word Ether, which called poetically to a material non-existent, which, according to some ancient theories, it filled the space and acted as a support for the propagation of the energy through the universe
The Ethernet standard also known as IEEE 802.3, uses a logical topology and bus topology-physical star or bus
Originally used coaxial cable , although today it is usually used UTP cable. The speed of transmission of information by the cable is 10 Mbps. Today with Fast Ethernet, also called 100BASEX, working at speeds of 100 Mbps
The Ethernet networks use the method CSMA/CD (Carrier Sense Multiple Access with Collision Detection) for access to the medium
Token Ring (IEEE 802.5)
Although IBM already had previously marketed the local area network called a Cluster (in base-band, with coaxial cable, to 375 Kbps and up to a maximum of 64 computers) and PC Network (broadband, 2 Mbps and up to a maximum of 72 computers), it was not until the year 1985 when IBM announced its local network to more sophisticated : the Token Ring, which is a network ring token-passing
The different computers in the network are connected to the multistation access units, MAU (Multistation Access Unit), within which the ring is formed
Up to 8 workstations can be connected to each MAU, and can have a maximum of 12 MAUs, therefore a maximum of 96 stations
The maximum distance between the computer and the MAU is 50 meters (although you could reach up to 350 meters with higher quality cables), and between MAU is 135 meters (being able to reach 215 meters)
The cable that is normally used is twisted pair, with or without shielding, although coaxial cable or fiber optic
Arcnet
It is a network base band, which transmits at a speed of 2.5 Mbps, with a topology hybrid star/bus. This system was developed in 1978 by the company Datapoint, although it was powered in the world of microcomputers by the company Standard Microsystems
Arcnet is based on a scheme of step signal (token passing) to manage the flow of data between the nodes of the network
All of the computers on the network are connected in star to a central dispatcher called the HUB active. The maximum distance between the computer and the HUB active must be less than 660 meters. The HUB's assets may also be connected to HUB liabilities, by connecting a maximum of 3 computers to each passive HUB. The maximum distance between a workstation and a passive HUB is 17 meters. You can connect more than one HUB is active, distancing himself between them to a maximum of 660 meters. In total, the maximum number of work stations must not be greater than 255
Subnets
When a LAN grows, it may be necessary or advisable for the traffic control of the network, it is divided into smaller pieces called network segments (or simply segments)
As a result, the network is transformed into a group of networks, each of which needs an individual address
Routers join or interconnect network segments or entire networks, taking logical decisions regarding the best path for sending data through an internetwork, and routing the packets to the segment and the output port suitable
Connection of a local network to the Internet
Basically the connection will be with a modem or a router that will allow us to connect to the lines-PSTN, ISDN, ADSL or cable
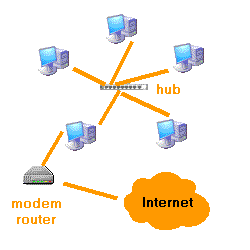
The connection can be single-user, that is to say, only a position in our network has direct connection to the Internet, or multi -, in which through a router, all connected to the Internet. The router can operate in single-user or multi-seat. In the connection desktop, this is received by a team of our network and the operation is the same as in the case of a modem
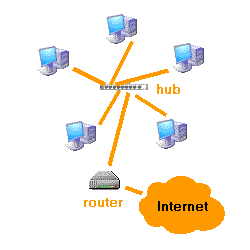
In both cases, each computer will have an IP address of the local network. This address must be one of the values reserved for local networks
In the first case, the computer that connects to the Internet, you will get a public IP
To share your connection with other computers you must do the routing and masking, that is to say, must be able to distinguish the IP requests from the Internet to the local network and you need to mask the requests of other computers as their own, and then pass the response to the team that has made
Yes the computer that connects to it runs under GNU/Linux, its IP address is defined as a gateway on the other computers. If the computer that connects to it runs under Windows, you often use software called a proxy, they configure each program to use the proxy
In the second case, the router will have two IP addresses, one local network and the public Internet that get by the connection. The router will perform routing and masking, and is set as the gateway on the other computers of the network
In the first case, the computer with connection, you can offer services of the Internet with its public IP. Can be mounted on a web server, an FTP server , a mail server...
In the second to move services to computers on the network, using the protocol NAT (Network Address Translation). In such a protocol is configured, the requests for the port, indicating the IP address and port of the computer to which should be moved
The topology of the local networks
The topology is the geometric form of placing equipment and cables that connect them
There are three possible ways of connection:
- Point-to-point
It will join two computers without going through an intermediate computer - Multipoint
Multiple computers share a single cable - Logic
The computers communicate with each other, whether or not there is physical connection directly between them
The study of the topology is based on finding the most economic and efficient way of connecting all users to all resources of the network, while guaranteeing the reliability of the system and wait times low
When the local networks are not too small, it is common for the mixture of topologies, giving place to other as a the star extended, a tree or hierarchical
Topology in the mesh
This topology is used when there can be no interruption in communications. So, each computer has its own connection to the other computers. This is also reflected in the design of the Internet, which has multiple routes to any location
Evidently, it is the topology that is most expensive for the amount of cabling and connection devices required. Is usually set between teams that need uninterrupted connection

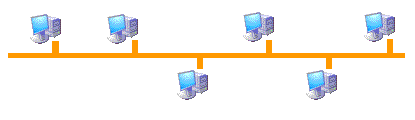
Topology in bus
Uses a single segment to which all the computers are connected directly. Is the network of minor wiring. It was the most initially used on a small local network. Its biggest drawback is that if a link fails, fails across the network. Sometimes used for backbone connections, for example, to connect different floors of a building
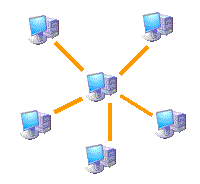
Star topology
Connects all computers to a central computer through a point to point connection. The teams pass the information to the central computer and relayed to the computer to which it is addressed. If the central computer fails, it obviously fails the entire network. The central computer is a server and requires the maintenance of specialized staff. The size and capacity of the network are directly related to the ability of the core team
A star topology extended connects individual stars together by connecting hubs or switches. This topology can extend the scope and coverage of the network
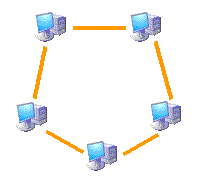
Ring topology
This topology connects a computer with the following, and the last with the first, that is to say, they form a circle of point to point connections between computers contiguous. The messages go from one computer to another until it reaches the proper
The communications protocol must avoid conflicting situations when using the shared medium. Sometimes there is a control center which assigns the shift of communication
Logical topology
The logical topology of a network is the way computers communicate through the medium
The two types of topology most common are:
- Topology broadcast
Each computer sends its data towards all the other computers through the network. The stations do not follow any order to use the network, the order is the first thing that enters, the first thing that is served. This is the way it works Ethernet - Topology for transmission of tokens
The transmission of the token controls the access to the network by transmitting a token-mail to each team sequentially. When the computer receives the token, it means that it is your turn to use the network. If you do not have data to send, it transmits the token to the next computer and the process is repeated
Two examples of networks that use the transmission of tokens are Token Ring and the Interface of distributed data for fibre (FDDI). Arcnet is a variation of Token Ring and FDDI. Arcnet is the transmission of tokens in a bus topology
The logical topology gives rise to the definition of protocols to establish how to perform the communication
